Here, I challenged the reverse-engineering skills of the participants. The challenge consists of a Binary which runs a physics simulation that drops balls into a jar.
Alongside the challenge, you are provided with an array of "secret numbers". (Those really are indices inside a array of physics objects)
Visualizing the physics objects, highlighting the indices inside "secret numbers" yields this result:
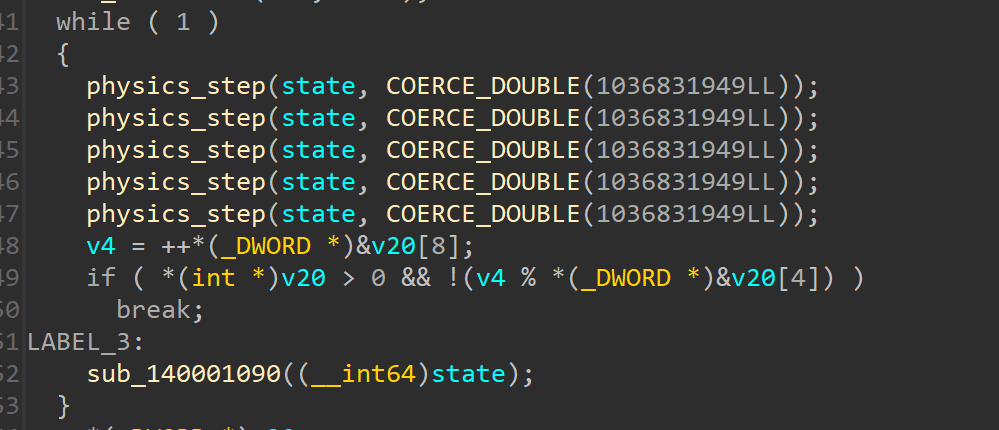
Taking a look at the binary in IDA, we can easily spot the main loop of the simulation. 
Now that we know how the physics simulation steps, we can hook the function like this: (this can be accomplished using any hooking library of your liking, see [0], [1] for suitable examples)
void *o_run_simulation;
void
Looking at the memory layout of the running application, inspecting state yields this: 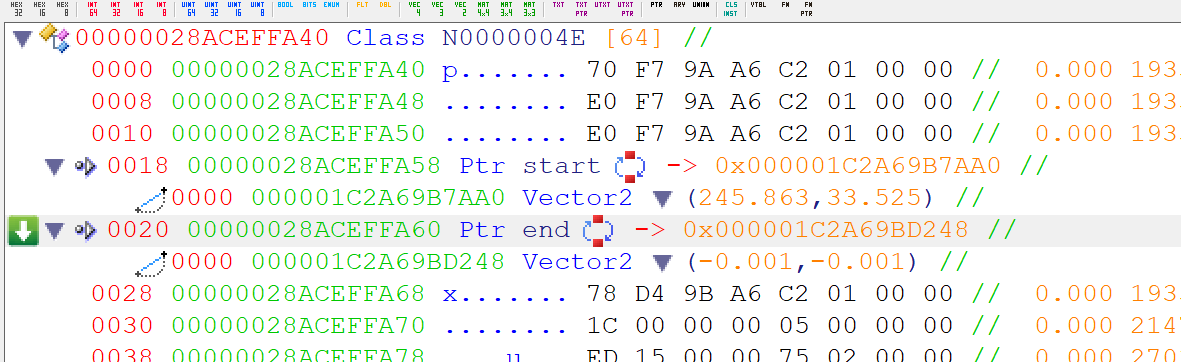
(As +0x18 and +0x20 are pointing to values that seem rather close, it's fair to assume they're start and end pointers)
Updating our hook to
uintptr_t physics_objects = state + 24;
auto it = *;
auto end = *;
auto ball = 0;
while
;
yields the video seen above.